Royal Military College of Canada
Department of Electrical and Computer
Engineering
EEE473 Computer Network Design
Dr G.S. Knight
Prof S. Leblanc
Lab 6
Network Address Translation
References
-
- hping3
Manual
- packet-filtering-HOWTO.html
References
hping
manual
Introduction
This Exercise is an introduction to Network Address Translation (NAT). NAT
is often used to make all traffic from a protected, private network appear
to be originating from a single IP address. This can be done to allow many
machines to have access to the Internet when only a small Internet address
space is available for use (i.e. conservation of IP addresses). It can also
be used to "hide" the machines on the protected, private network. That
is, because the machines on the private network do not have externally
visible IP addresses they can not be directly contacted by machines outside
the private network. The machines on the inside must initiate communication.
NAT can also be used at the packet filter to direct all traffic addressed to
a particular IP address/port number, to a specific machine on the internal
network. You can also direct all traffic addressed to a specific IP address
in the external IP address space to a different IP address in the address
space of the protected, private network.
How
does NAT fit in with iptables packet filtering
Recall that you looked at the FORWARD, INPUT and OUTPUT chains in the
iptables/netfilter firewall. These chains were part of a 'table' called the
'filter' table. You did not specify this table when writing iptables rules
because the filter table is the default table. There is another table
defined for the iptables/netfilter firewall called the 'nat' table. The nat
table has two chains that we will be looking at in this exercise: the
PREROUTING chain and the POSTROUTING chain. Packets are processed by these
chains in the decision diamonds in Figure 1 before the packets proceed for
processing on the 'filter' table FORWARD, INPUT or OUTPUT chains.
Figure 1 - Configuration of chain
processing
Recall that the main targets we used when a chain rule was matched in the
'filter' table chains was DROP or ACCEPT. The main targets used on the 'nat'
table chains will be MASQUERADE, SNAT and DNAT. The target MASQUERADE is
usually used on the POSTROUTING chain and causes the source IP address of
the packet to be substituted for another address (by default the address of
the firewall). Masquerading also keeps track of these substitutions so that
packets returning from the Internet have the correct reply address
substituted back so the packets can reach their correct destination on the
internal network. The SNAT and DNAT targets are used to specify specific
source and destination address translations respectively.
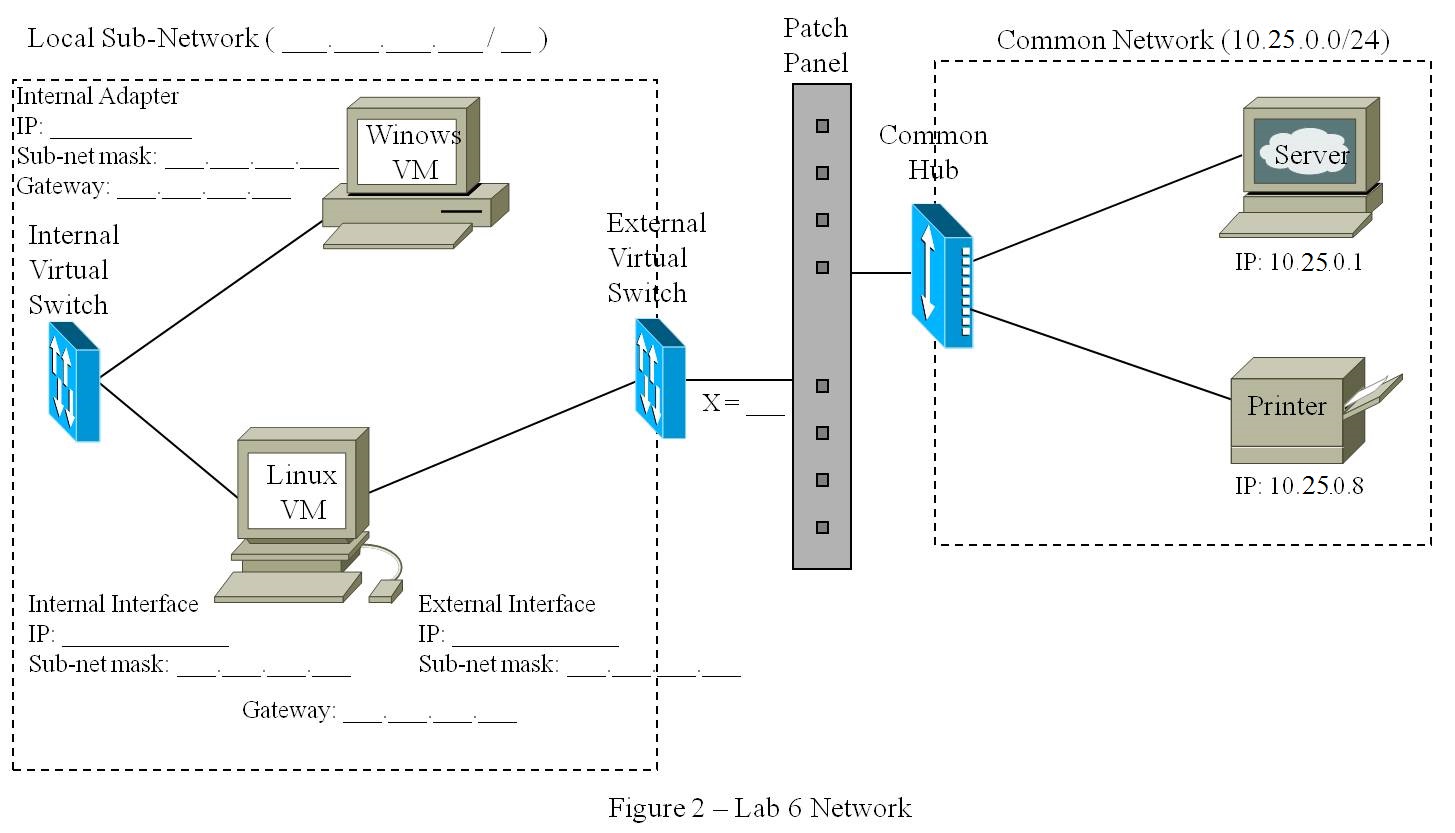
Exercise Setup
Set up your lab environment according to the
specifications below, and annotate Figure 1 accordingly. Note that it is
the same setup as used in Lab 6.
- Your Local Network is defined by
10.0.x.0/24, with the following host specifications:
- The Linux VM IP address is
10.0.x..200 (recall that x = 100+X)
- The Windows VM IP address
is 10.0.x.100
- Note that the subnetwork gateway is the Linux
VM
- The Common Network is defined
by 10.25.0.0/24, with the following host specifications:
- Your Linux VM address is
10.25.0.y (recall that y = 200+X)
- A Server at 10.25.0.1
- A Printer at 10.25.0.8
- The subnetwork gateway is the Server
Ensure that you
have IP forwarding turned on to enable the Linux
VM to act as a router.
- sudo
sysctl net.ipv4.ip_forward=1
- sudo
route add default gw 10.25.0.1
From Lab 6 you had a iptables_rules.sh
file with the following rules:
#!
/bin/sh
alias iptables='sudo iptables'
iptables --flush
iptables --policy INPUT DROP
iptables --policy FORWARD DROP
iptables --policy OUTPUT DROP
iptables -A OUTPUT -p icmp --icmp-type echo-request -j ACCEPT
iptables -A INPUT -p icmp --icmp-type echo-reply -j ACCEPT
iptables -A FORWARD -s 10.0.x.0/24 -p icmp --icmp-type echo-request -j
ACCEPT
iptables -A FORWARD -d 10.0.x.0/24 -p icmp --icmp-type echo-reply -j
ACCEPT
iptables -A FORWARD -s 10.0.x.0/24 -p tcp --dport 23 -m state --state
NEW,ESTABLISHED -j ACCEPT
iptables -A FORWARD -d 10.0.x.0/24 -p tcp --sport 23 -m state --state
ESTABLISHED -j ACCEPT
Verify the current rules:
Recall from Lab 6 the shell script you wrote to implement your iptables
rules. If you still have this file then use it now. Otherwise, recreate iptables_rules.sh
from Lab 6; remember to make the file an executable using chmod
755. Then run the shell script:
- ./iptables_rules.sh
;
iptables
-nvL
Also
recall that the laboratory
instructor will need to add a route to the main
lab router that tells it that your router/firewall is the gateway
for your new LAN.
- route
add -net 10.0.x.0 netmask 255.255.255.0 gw 10.25.0.y
NAT Masquerade
You will configure your firewall to hide the internal network behind the
firewall external interface (10.25.0.y).
Before you do this run tcpdump on both
the Internal and External interfaces of the Linux
VM:
- Open two new terminals:
- In one terminal sudo tcpdump -i internal_interface -nv port 23
- In the other terminal sudo tcpdump -i external_interface -nv port 23
Now, run telnet from the Windows VM
to the Server. Examine the
source and destination addresses in the telnet traffic on either side of the
firewall.
- Attach a sample of this traffic in your lab report.
- Log out of alice's account on
the Server.
Return to your original terminal, where you are administering the firewall.
View the current nat rules;
there should be none.
Now, add a masquerading rule to your iptables_rules.sh
file.
iptables -t nat --flush
iptables -A POSTROUTING -t nat -o external_interface
-s 10.0.x.0/24 -d 0/0 -j MASQUERADE
Refresh the rules:
- ./iptables_rules.sh
;
iptables
-nvL
-t
nat
Be sure you understand what each part of this rule does. This command adds a
rule to the POSTROUTING chain of the nat table, which matches packets
leaving/output on the external interface that originate from subnet 10.0.x.0/24
and are destined for any
network. The target of the rule (i.e. the action to take for packets
matching this rule) is to Masquerade, i.e. substitute the source IP address
for the firewall address and record this substitution in a table so the
reverse substitution can be performed on returning packets.
Again, run telnet from the Windows VM
to the Server. Examine the
source and destination addresses in the telnet traffic on either side of the
firewall. What has changed?
- Produce a tcpdump of the traces and highlight the changes.
Attach this to your lab report.
Challenge
for the adventurous
The NAT masquerading you just looked at dealt with
address translation for traffic initiated from within your internal
private network. What about traffic originating on the outside; how does
it find important servers like ns, mail or www that are on a DMZ inside
your firewall if it is using NAT masquerading?
Examine the sections of the Quick_HOWTO:
Linux_Firewalls_Using_iptables guide titled:
- Port Forwarding Type NAT
- Static NAT
Write the rules that would allow external machines to find your ns,
mail or www server inside your NAT masquerading
Submit your lab report by e-mail. Place files together in a zip
file before sending. Include your report and network traffic dump files.
Don't forget how important the discussion section of the lab is.